The mid-decade challenge for the U.S. Intelligence Community is winning the accelerating race for actionable insight to enable U.S. statecraft in a more information-rich and geopolitically competitive world.
For the first time since the Cold War, the United States faces a rival – the People’s Republic of China – that is competing globally across the economic, political, social, and military domains to lead, if not dominate, the international order. For the U.S. Intelligence Community, this rivalry will shape not only what U.S. leaders ask of it, but also how it must evolve to meet this challenge. In a rivalry with a technological and economic near-peer, providing insight into emerging technologies and the organizations that field them is as important as understanding the traditional political and military institutions of a state.1
In addition to the geopolitical rivalry, the exponential increase in surveillance, monitoring, and collection technologies are creating avalanches of data. Like all U.S. Government organizations, the IC faces challenges to collect, process, and analyze it. Once government-unique capabilities, like geospatial2 and signals intelligence,3 have been commercialized. Private companies can now provide tailored analytic products to U.S. Government consumers on breaking events, sometimes ahead of the IC, in part because they are equipped to use AI and other emerging technologies. These companies can also select contracts or exploit opportunities that specifically showcase their strengths.4 Meanwhile, policymakers’ demand for insight across an ever-broader array of issues may lead them to turn more frequently to the private sector and academia, or to try and find the data they need on their own in the public domain.
In a rivalry with a technological and economic near-peer, providing insight into emerging technologies and the organizations that field them is as important as
understanding the traditional political and military institutions of a state.
For its part, the IC remains predominantly human-centric, relying on methods that are manually intensive and lack scalability, despite some pockets of technological excellence. Compounding that problem, the IC is still transitioning from countering terrorism to supporting the geopolitical competition with the PRC (and Russia). However, the IC remains essential. Amidst a flood of data and opinion, the IC’s emphasis on objectivity and providing insight independent of policy give it a vital role in supporting leaders grappling with difficult decisions.
…the IC’s ability to provide competitive advantage to U.S. policymakers will hinge on whether it can master emerging technologies, including AI, to integrate more and more diverse information across all domains.
IC leaders appear to understand the challenges of this new era of techno-economic competition. They were among the first in the U.S. Government to experiment with AI,5 with numerous AI projects,6 organizational shifts,7 and new efforts to capture data outside government channels.8 They recognize that once-unique U.S. collection capabilities are now known and used by foreign intelligence services. The PRC and other hostile actors exploit this knowledge and the opportunities afforded by ubiquitous technical surveillance to become global counterintelligence threats.9 As the PRC builds out digital infrastructure globally, U.S. intelligence will more frequently operate where Beijing can apply its own technology-enabled tools, including AI and biotechnology, to expose its operations.10 The IC leadership’s understanding and attempts to address the problem, however, have not yet translated into sustainable, community-wide change.
In this new context, the IC’s ability to provide competitive advantage to U.S. policymakers will hinge on whether it can master emerging technologies, including AI, to integrate more and more diverse information across all domains. The IC’s ability to unlock new insights in support of U.S. statecraft will hinge on whether it can take action in the following areas:
- Adapt to the technological era and rivalry through digital transformation by integrating people, process, and technology to exploit a wider body of data in support of national security;
- Leverage insights and information through open source capabilities by creating a dedicated, technology-enabled open source entity to support U.S. decision making;
- Create new capacities to capture and master economic, financial, and technological intelligence by establishing a National Techno-Economic Intelligence Center to serve as an economic “nerve center” for U.S. policymakers; and
- Counter foreign adversarial influence operations by preemptively exposing them when possible, warning of them when strategically consequential, and alerting senior U.S. Government officials who may be targeted by such operations.

This transition will not be easy. The White House and Congress must set the direction while IC leaders sustain focus within the bureaucracy for forward movement. Policymakers and members of Congress must agree to a vision on how to urgently reform the IC based on the current technology trends and geopolitical threats. The closed nature of U.S. intelligence — a requirement for keeping secrets — has often allowed inertia to persist. When united under a common goal, however, the IC is capable of remarkable transformation as it demonstrated after the September 11, 2001, terrorist attacks. The stakes of the moment demand that U.S. intelligence overcome the bureaucratic resistance to change.
Adapting U.S. Intelligence for the Digital Era
U.S. intelligence is capable of delivering on the seemingly impossible and the once-unthinkable. The IC was able to successfully warn the White House, Ukraine, and its allies of the Russian invasion long before its actual occurrence.11 The early and rapid declassification of this intelligence countered Russian disinformation credibly, dissuaded the possibility of false flag operations, and undermined the Kremlin narrative.12 This kind of performance is made possible by the IC — along with its U.S. Government partners — operating the world’s largest constellations of human and machine sensors located anywhere from undersea to outer space. The IC benefits from the accumulated data even when it struggles to process it, and all while looking at the world outside the range of its sensors. U.S. intelligence faces a paradox of simultaneously having both too much and too little data.13
As the IC becomes increasingly involved in countering rivals and enabling U.S. and allied actions, one key to winning the techno-economic competition will be employing emerging technology tools, especially AI, to turn troves of data — and the correct type of data — into a wealth of intelligence that enables U.S. policymakers to act.
Mastering AI and emerging technologies has the potential to transform the IC. Top-down leadership is needed to drive and sustain this transformation. Success in AI and emerging technologies starts with the right leadership culture that is committed to the endeavor and willing to devote time and resources.14 Transformation requires adherence to a coherent vision that aligns strategies, actions, incentives, and metrics. IC leaders must understand AI and emerging technologies, and their limitations, to maximize the opportunities the technology can offer. To achieve this, promotion within the senior executive service ranks should require executive education on AI and emerging technologies.15
The Director for National Intelligence (DNI), Undersecretary of Defense for Intelligence, and the directors of Central Intelligence Agency, Defense Intelligence Agency, National Geospatial Agency, National Reconnaissance Office, and National Security Agency, in particular, must take the lead because their agencies are well-equipped to serve national missions. They are also uniquely positioned to lead their own staff and agency in transforming the bureaucracy.
Creating a technology-enabled and AI-driven IC will need to be a community-wide effort. Over the years, the IC has developed several AI strategies and implementation plans,16 but they have been unevenly implemented across the community and individual agencies. The IC needs a single, cohesive strategy for transformation to turn isolated initiatives into a community-wide technological revolution. IC leaders and their designated technology leadership should prioritize projects that build internal tech expertise, improve data standardization and architecture, and support emerging tech adoption at scale across the IC.
Successful, at-scale digital transformation requires the right combination of people, processes, and technology. The IC requires a broad foundation to ensure that emerging technology services can be built, scaled, and effectively employed across mission areas. It needs people with the right expertise to advance technology; processes to manage areas where humans and technologies converge; and the right technology to store, process, and move data at immense scale. Integrating these elements is a challenge for any large enterprise, upsetting traditional career paths, workflows, data management, and technology integration. Shifting the IC’s practices will require standardizing and contextualizing data for broader use, building a new digital backbone, and accessing necessary talent. As these elements come together, the IC would gain agility and efficiency in iterating on existing applications and applying them to new problems.
IC leaders and their designated technology leadership should prioritize projects that build internal tech expertise, improve data standardization and architecture, and support emerging tech adoption at scale across the IC.
To effectively counter adversaries and maximize the Intelligence Community’s potential, U.S. intelligence and its external stakeholders must refine their sense of risk. Avoiding risks in the short term is a sure way of creating long-term risks for intelligence failures. As the speed of information, technological innovation, and decision-making accelerate, the IC should reevaluate the risk across all aspects of the enterprise — including how data is shared, how technology is acquired, and how talent is recruited. It also must include the risk of incremental changes or doing nothing. Sometimes, doing nothing can be the riskiest choice of all. Internally, this includes providing space for experimentation, tolerating failures, and ensuring that security practices support the intelligence mission. Externally, the IC must partner with Congress and the Administration so that external stakeholders accept reasonable risk-taking.
Building the conditions for a tech-enabled Intelligence Community also requires new security approaches that bring critical expertise and technology into the community. The IC has an opportunity to update its security practices and redefine the meaning of successful security. Success should be the safe employment of people and technology needed to execute its digital age mission facing an all-domain rival. Current security practices prevent many qualified candidates that have lived in the PRC from working in the IC.17 These security practices also slow down the adoption of needed, advanced commercial technology in favor of retaining older, government-approved technology.18 The IC needs dynamic, digital age-aware security practices that are fully aligned with overall national security and IC objectives.
U.S. intelligence leadership needs to revisit security processes and the preoccupation with counterintelligence risk minimization. Risks cannot be avoided in the world in which the IC is operating. Attempting to do so places barriers between U.S. intelligence and the resources, both human and technological, needed to adapt to the rivalry with the PRC and the digital era. The current security system was originally constructed to address threats against IC interests that exploited relatively small, stable, and predictable attack surfaces. The individualization of data, mobile telecommunication, social media, and the centralization of personal information on databases creates opportunities for hostile intelligence services to target IC employees and contractors without ever coming face to face with the individual.19 The attack surfaces that security now seeks to protect are constantly expanding and evolving in unpredictable ways.20 Yet, the fundamentals of how people and technology are cleared have not significantly changed in decades.21
Accessing tech-savvy talent requires the Intelligence Community to adopt more flexible approaches for hiring and retention. The IC possesses three advantages over the private sector that ensure people will want to join, and even return, to public service. The first is a sense of purpose. The second is a unique problem set. The third is a sense of stability. However, the IC – and the U.S. Government more broadly – will continue to be challenged to compete directly with the private sector for compensation. Salaries for AI talent, in particular, continue to rise along with the demand in the private sector. The competition for technical expertise in the current market puts the IC at a disadvantage in hiring top-level talent.22 Beyond this technical talent, the IC also needs people adept at shaping how the community manages AI and other emerging technologies.
More flexible approaches to recruitment and career development would allow the IC to better harness expertise and stay at the cutting edge of technological development. The current personnel system generally does not reward individuals who move between the private sector and the IC. This internal orientation was less of a problem when significant technological innovation occurred inside the government, but the private sector has taken the lead in emerging technologies.23 Only by allowing or facilitating government employees to move in and out of government or by developing personnel exchange or fellowship programs with the private sector will the IC ensure it has regular access to talent knowledgeable and capable of applying leading technologies. The National Reserve Digital Corps, proposed by the National Security Commission on Artificial Intelligence, could enable this exchange.24 Yet another talent pipeline for the IC could be a potential U.S. Digital Service Academy, also proposed by the NSCAI.25
As it embraces AI, the Intelligence Community can learn from other complex organizations, while adapting the lessons to its specialized missions. Large, complex companies across a range of industries and employing tens of thousands of people have moved from the industrial age to the digital age by integrating AI and other emerging technologies throughout their operations. The IC has a unique mission and may have unique features, but some of the core principles for digital transformation appear consistent and can be adapted and leveraged to the IC’s needs. These principles include a commitment from leadership, integrated digital infrastructure, and organizational capacity – all developed and applied in stages over time. But the private sector also provides negative examples of how AI initiatives fail. By treating digital transformation as a series of disconnected, independent experiments, rather than a disciplined, multi-stage process, organizations set themselves up for failure.26
Beginning with a focused leadership aligned behind a single strategy for digital transformation, U.S. intelligence should progressively move its people, processes, and technologies through a series of phases.27
The DNI should sponsor the creation of a Digital Experimentation and Transformation Unit to run pilot projects that address community-wide challenges on talent, processes, technologies, or acquisition as identified by the DNI and IC agency directors. The unit should be sponsored and empowered by the DNI, with one of the intelligence agencies serving as the executive agent, and with representatives from each member of the intelligence community. The purpose would be to identify and apply the best available technology and expertise in the United States to select community-wide problems. The DNI would also need support from Congressional appropriators to ensure the office has the necessary time and support to solve the selected problems. The pilot projects should address a key aspect of the people, processes, technology, and acquisition needs of the IC to accelerate its digital transformation. All projects would need to include programmatic analysis for each participating IC element to ensure successful projects are sustained beyond the new unit. The initial focus areas could include:
- The recruitment, vetting, and employment of personnel that possess needed expertise and/or meet some high-risk criteria;
- The improvement of systems interoperability across the IC; or
- The automation of cross-collection platforms tipping and queuing at the edge to improve IC indications and warning capabilities.
Leveraging Open Source Capabilities
In an age where most data resides in the open world,28 the IC risks surprise and intelligence failure without a robust open source intelligence capability. The exponential growth in publicly and commercially available information has outpaced the IC’s capability, or anyone’s for that matter, to fully harness open source in support of U.S. decision making and policy.29 This has come on top of the decline in the collection, processing, and usage of open source materials through the evolution of IC open source initiatives from the Foreign Broadcast Information Service (FBIS) to the Open Source Center to the Open Source Enterprise (OSE). Moreover, less attention to collection, user-unfriendly platforms, and overzealous security practices have limited U.S. intelligence analysts’ effective access to and use of government open source resources over time.30
To be sure, there are no substitutes for U.S. eyes and ears inside the hallways of foreign capitals. However, the integration of open source data as part of an automated intelligence cycle could enable and focus clandestine intelligence collection on the most important collection targets. Moreover, machine learning models can be employed to label, classify, cluster, and connect data to publicly validate U.S. claims about the malign activities of the PRC and Russia without compromising the IC’s sources and methods.
The U.S. Government must address this and build a tech-enabled open source entity, particularly one with the potential to drive speed of execution, experimentation, and collaboration.
The U.S. Government must place the collection of publicly available information, acquisition of commercially available information, and their processing at the center of its renewed open source efforts. Calls for an effective open source entity date back to the Cold War.31 IC experts have long estimated that over 80 percent of the information needed to support intelligence, military operations, public diplomacy, and other policy initiatives can be acquired publicly or commercially.32 As the potential of publicly available information grew well beyond print and broadcast media, so too did the calls for improvements to the IC’s open source capabilities.33 In more recent years, independent commissions and various studies have reiterated these calls. In 2005, the Commission on the Intelligence Capabilities of the United States Regarding Weapons of Mass Destruction stated “The Intelligence Community does not have an entity that collects, processes, and makes available to analysts the mass of open source information that is available in the world today.”34 Subsequent studies of open source intelligence have reinforced the need for a central entity within the Intelligence Community or U.S. Government. While calls for an open source organization are not new, the United States can no longer ignore the value of publicly and commercially available information; the urgency of the techno-economic competition demands action immediately.
A necessary first step in harnessing the potential of open source data is for all the U.S. Government departments and agencies to significantly improve their sharing of information with one another, which is something that the current Federal Data Strategy already encourages.36 But the other critically important step is for the IC, and even more broadly, the U.S. Government to address the collection, acquisition, and processing of foreign publicly and commercially available information.
The U.S. Government should create a new, well-resourced institutional home for open source collection, acquisition, processing, and analysis. The difficulties and costs of collecting open source data, the specialized skills required to handle such data, and privacy concerns related to some of the data suggest that this mission can only be addressed by an entity tailored for the task. A clear institutional home would also provide clarity of purpose and mission focus.
As foreign targets learn how researchers or governments might exploit publicly available information to inform future policy actions, they can be expected to adjust and adapt their activities accordingly – changing URLs, putting access controls in place, altering content, or even removing it entirely.37 The U.S. Government needs to position itself now to exploit such closing windows of opportunity. With U.S. rivals also increasingly aware of what open source researchers are doing online and the potential policy consequences of such research,38 professional tradecraft is more frequently needed to access quality open source information across barriers put up by rivals, such as requirements for true names, local phone numbers, and official identification numbers.39
Normalizing the use of open sources among all-source analysts does not address this problem. Those analysts, whose expertise lies in a regional or functional specialty and supporting decisions, cannot replace the role of dedicated collectors.40 Furthermore, the procurement and collection of publicly and commercially available information demands a cadre of professional collectors with both domain expertise and technical knowledge to discern credible sources from those that are not, and to communicate the necessary context as open source reports are disseminated for wider usage.
Finally, the cost and privacy concerns associated with commercially available information require deliberate acquisition and management efforts. Private companies now have their own sensors. They collect digital data on a range of relevant economic and human activities. Such data, however, is not free. More importantly, it can include information on U.S. persons, necessitating careful handling to protect their privacy and to ensure that agencies receive only the data they are allowed to receive.
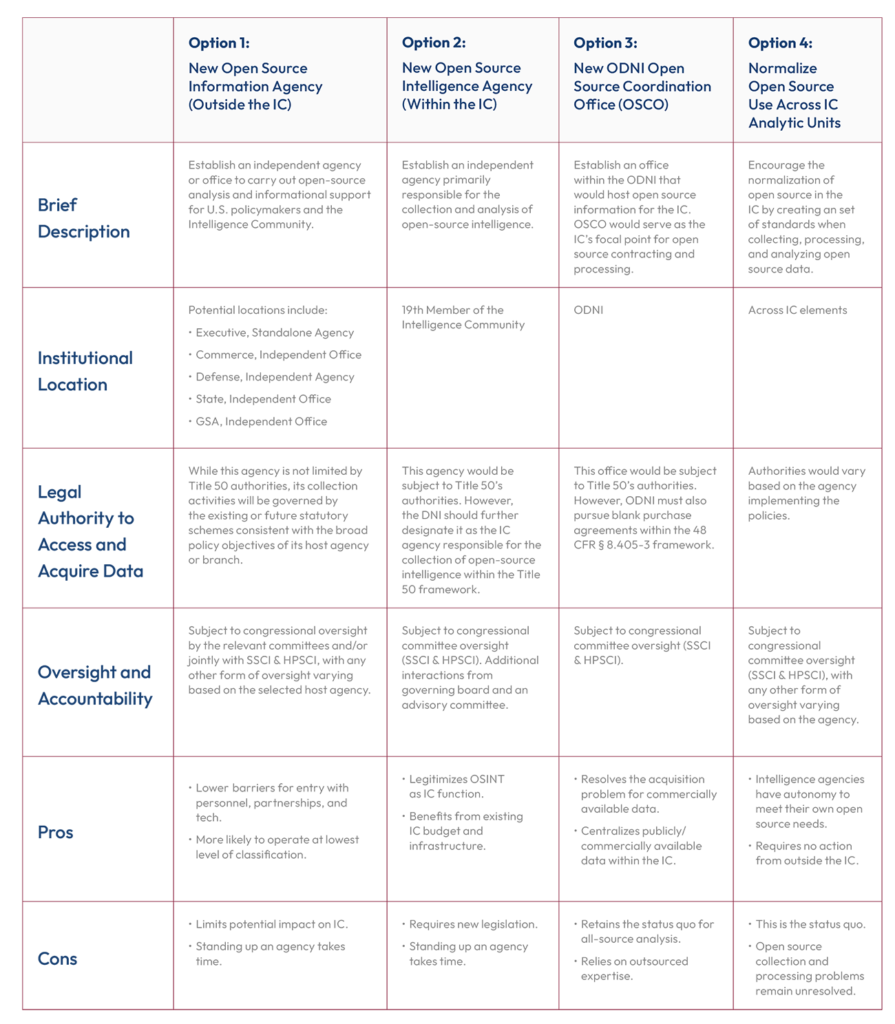
The U.S. Government has a number of options to choose from on how to stand up an open source entity. While the precise organizational model for an open source entity is secondary to ensuring that it meets the U.S. Government’s needs, there are several options to choose from to address the imperative of the open source mission. In assessing the various options, U.S. Government stakeholders should be mindful of several attributes that could make such an open source entity a success: (1) It should be connected to and have a voice within the IC, regardless of where it sits; (2) It should have a hybrid workforce, including cleared and uncleared personnel, and develop expertise through time on target and promotions; (3) It should have a clear collection and processing mission; (4) It should serve as a focal point for U.S. Government absorption and integration of commercially available data; (5) Other IC agencies and the U.S. Government, more generally, should be able to access, search, and use this data for their own queries and AI projects; (6) Such an entity should also serve as a gateway through which nongovernmental analysts, academic researchers, and the public writ large could access open source information; and (7) It should be able to liaise with counterparts among allies and partners.
This entity could be organized in one of three broad ways. The first is as an independent agency within the executive branch, either as an independent office reporting to the White House or an agency reporting to an existing department. Potential departments include the Departments of State, Defense, Commerce, or the General Services Administration. The second way is as an IC entity, its 19th member, primarily responsible for the collection and analysis of open source intelligence. The third way is a coordinating office within the Office of the Director of National Intelligence that would host open source information for the IC, deconflict the IC’s open source activities, coordinate purchasing, licensing, and managing of commercial data for the U.S. Government, and serve as a point of contact for the external open source research community. One final option would not rely on establishing a new entity; rather, it would entail the methodical integration of open sources in greater quantities in all-source analysis and the creation of a set of standards when collecting, processing, and analyzing open source data. This option would likely require changes to analytic training and tradecraft, review processes, and resources.41
Strengthening U.S. open source capabilities provides one of the best “use cases” for shifting the IC practices critical to mastering artificial intelligence. In strengthening open source, the IC could also make it into the leading “use case” for AI-enabled transformation because:
- The ability to transfer commercial AI approaches to open source problems would streamline its path to success and allow an open source entity to become operational and scale faster.
- The demand for open source intelligence is profound, and multiple agencies can leverage open source data for their own insights. Using AI would enable the curation and improved vetting of open source data at scale.
- The relative transparency of an open source agency would ensure that AI and emerging technologies achievements and lessons learned would remain visible to other individual agencies and help guide them in their own technology transformation. The current pedagogical approach of learning from intelligence failures and keeping successes secret is inadequate in the age of AI and emerging technologies.
As part of the transition toward a new, open source entity, all-source analytic units should run a series of internal pilot projects to build skills in exploiting open sources with AI tools. Open source analysts must tackle the same intelligence topics as collectors and analysts within other intelligence disciplines to be taken seriously. Individual IC entities should establish AI-empowered red teams composed of open source analysts to assess publicly and commercially available data for comparison with classified products. Pilot red teams would provide an opportunity to train open source analysts on AI tools, and simultaneously demonstrate the utility of both AI and open source data to intelligence analysis writ-large.
These pilot projects should be explicitly designed to complement an overarching strategy that aims to catalyze the Intelligence Community’s transition into a modern enterprise with expertise in all intelligence disciplines – including open source. Without a broader plan, such projects could end without a measurable impact on the wider U.S. intelligence enterprise, as occurred with experimental projects like Open Source Works.42
The U.S. Government must attempt to make select open source products a utility available to all Americans, creating a virtuous cycle of expertise between government and non-government experts. The intensity and stakes of the current techno-economic competition require a higher degree of shared knowledge and understanding across U.S. society. The opaque and controlled information environments of U.S. rivals, especially the PRC, require a high degree of knowledge to identify the authoritative signals that these governments publish for internal and external audiences. From the 1940s to 2013, when the service ended, IC open source experts helped curate and publish foreign media translations and analyses for public use.43 U.S. academics, in turn, used these resources – often not readily available elsewhere – to shed light on important developments in the PRC and other closed societies, which in turn informed U.S. policymakers. The U.S. Government should recreate this service for an age of AI and emerging technologies. It must treat open source as a utility that enables the IC’s ability to provide insight to Americans outside of government and harness insights from these Americans to inform policymakers.
The intensity and stakes of the current techno-
economic competition require a higher degree of shared knowledge and understanding across U.S. society.
Creating Techno-Economic Intelligence
U.S. intelligence capabilities are pivoting toward the bipartisan U.S. policy statement that “economic security is national security.”44 U.S. intelligence must retool for economic competition in order to defend Americans’ standard-of-living, support a U.S. Techno-Industrial Strategy,45 and protect the interests of the United States and its allies around the world. This re-tooling should be based on an initial net characterization of the techno-economic competition with China.
U.S. intelligence should leverage insights from the private sector to improve the picture of U.S. adversaries’ economic, financial, and technological capabilities. U.S. intelligence should leverage, not recreate, the private sector’s collection and analysis of economic information. Forming public-private partnerships with industry, Wall Street banks, consulting firms, academia, and the business media would enable U.S. intelligence to efficiently build upon their sector expertise, broader resources, on-the-ground presence, and market-based insights, and marry them with IC information to create a more comprehensive intelligence picture. The Department of Commerce, in particular, should expand its techno-economic intelligence capabilities and set up an office responsible for fusing industry data already collected by Commerce with U.S. intelligence reporting to produce sector-specific techno-economic threat intelligence for industry and policymakers, while ensuring the necessary safeguards to protect the privacy of American citizens and proprietary information of U.S. companies.
The U.S. Government should establish a National Techno-Economic Intelligence Center. The U.S. Government should create a National Techno-Economic Intelligence Center that can coordinate economic threat information and work closely with policymakers on responses to these threats.46 The center should be established under a well-resourced sponsor that can support its mandate within government. Using AI to collect and process economic information at scale, this economic “nerve center” would be able to make economic assessments and forecasts and fuel innovation in economic modeling. This center, with analysts trained for techno-economic analysis, would warn of U.S. economic vulnerabilities, make sense of rivals’ grand strategies,47 send warnings to U.S industry about economic threats, especially intellectual property theft, and evaluate opportunities to deploy tools of economic leverage.
U.S. intelligence needs the authorities, capabilities, and incentives to make techno-economic net assessments. The IC should be able to provide policymakers with an economic “order of battle” for our strategic rivals that maps out and details critical supply chains, technologies, industries, and companies. U.S intelligence needs the authority and internal guidelines to conduct these net assessments informed by an awareness of the U.S. techno-economic landscape48 while ensuring appropriate privacy safeguards for U.S. citizens. It should prioritize supporting other government centers tasked with providing technology net assessments, such as the Office of Global Technology Competition Analysis proposed by the American Technology Leadership Act49 (and included in the Senate version of the Intelligence Authorization Act for FY2023)50 or a Technology Competitiveness Council (TCC) proposed in Chapter 1 of this report.
U.S. intelligence collection should include adversary scientific and technological research that has dual-use purpose or application. The United States has enjoyed the position as the world’s dominant economic and technological power since World War II,51 reducing somewhat the need for IC awareness of adversarial scientific and technological research. However, growing research on dual-use technologies and their applications by U.S. adversaries that leverages innovations across military and civilian sectors requires the IC to expand its awareness.52 For example, the PRC’s economic growth over the last 40 years has brought it to a peer or near-peer status in a number of critical technologies, such as computer vision, next-generation mobile communications, and battery technology.53 The PRC’s national strategy for military-civil fusion, through which it integrates its civilian economy with its military industrial base, underscores that techno-economic competition carries directly over into traditional national security areas.54 The PRC’s domestic innovation base,55 aided through its theft of U.S. intellectual property,56 should be considered a U.S. intelligence collection priority, which can be employed to inform our own, government-led scientific and technological research efforts.
Countering Foreign Adversarial Influence Operations
The acceleration of
technological advancements and the emergence of new media platforms have enhanced the speed, reach, volume, and
precision of disinformation generated by foreign
adversaries.
U.S. rivals increasingly resort to the aggressive use of disinformation to target U.S. decision-making, reputation abroad, and social cohesion at home. Trolls, bots, and deepfakes deployed by the PRC’s cyber militias and Russia’s Internet Research Agency are also aiming at incremental erosion of key tenets of democracy until people question what is demonstrably true.57 The acceleration of technological advancements and the emergence of new media platforms have enhanced the speed, reach, volume, and precision of disinformation generated by foreign adversaries. The scale, scope, and snowballing effect of these influence operations make disinformation a particularly acute concern for national security. The U.S. Government must protect Americans from, counter the effects of, and disrupt adversary influence operations.
The U.S. Government – including the Intelligence Community – must counter foreign adversarial influence operations through early-stage countermeasures. Prior to Russia’s invasion of Ukraine, the United States and the United Kingdom engaged in what appears to have been deliberate disclosure and exposure of Russian malign intentions.58 This approach should be replicated whenever possible and suitable. Through early disclosures of anticipated physical or virtual malign actions, U.S. and allied governments could potentially deter or, at a minimum, “prebunk” them.59 The “prebunking” could help raise awareness among the domestic public, enabling them to sense and avoid misleading content proliferating in their newsfeeds.60
But deterrence-related and “prebunking” disclosures may not always be possible.61 The U.S. Government should also aim to identify and alert the public of foreign disinformation operations that seek to undermine the social cohesion of the United States. While such disinformation operations may not have an obvious tactical urgency, they can have

strategic consequences. The IC entities could collaborate on this endeavor with the Cybersecurity and Infrastructure Security Agency (CISA) and expand the National Cyber Awareness System62 to potentially alert the public about foreign disinformation operations of strategic import.
Finally, the IC can also publicly identify false narratives and themes propagated by U.S. adversaries that aim at the truth more broadly and at U.S. reputation abroad. This publicizing could be done for the purpose of encouraging and enabling private sector and academic researchers to examine them further. Independent expertise could thus be a force multiplier for a resource-demanding mission.
Identify a focal point that tracks, counters, and disrupts foreign-directed denigration campaigns against senior civilian and military leaders. Our adversaries are working to acquire, analyze, and weaponize data on DNA, dating preferences, shopping tendencies, social networking, and professional experiences of much of the U.S. population.63 Empowered by AI, this could allow foreign intelligence services to micro-target senior civilian and military leaders by denigrating them in the public domain and orchestrating character assassination efforts,64 which would put such senior leaders under considerable pressure and distract them from discharging their duties. At present, it appears that no entity in the U.S. Government is specifically tasked and resourced to track, counter, and disrupt such denigration efforts – and the collection efforts that support them. While further analysis of authorities and broader engagement of various stakeholders is required to recommend an institutional home, the imperative for establishing or designating an entity that focuses on this mission is already here.
The constant evolution of influence operations requires the Intelligence Community – and U.S. Government writ large – to incorporate new technologies and mitigation techniques quickly. Digital influence operations advance at an exponential rate, presenting the IC with the challenge of keeping pace.65 Leveraging tools like the content provenance standards of the Coalition for Content Provenance and Authenticity66 and DeepMind’s RETRO database67 could help the IC outpace adversaries by authenticating content origins and verifying information, respectfully, while embracing high speed human-machine teaming would increase overall speed of IC operations.68
1. Corin Stone, A Roadmap for AI in the IC, The Cipher Brief (2021); Amy Zegart, American Spy Agencies Are Struggling in the Age of Data, Wired (2022); Corin Stone, Artificial Intelligence in the Intelligence Community: The Tangled Web of Budget & Acquisition, Just Security (2021).
2. Todd Harrison & Matthew Strohmeyer, Commercial Space Remote Sensing and Its Role in National Security, Center for Strategic and International Studies (2022).
3. Cortney Weinbaum, et al., SIGINT for Anyone: The Growing Availability of Signals Intelligence in the Public Domain, RAND Corporation (2017).
4. Elizabeth Leyne & Yvette Nonté, Is the Intelligence Community Staying Ahead of the Digital Curve? A Survey of its Highest-level Customers and Leaders on the Challenges and Opportunities Ahead, Harvard University – Belfer Center for Science and International Affairs (2021).
5. Maxime Fischer-Zernin, Narrative Science: The CIA is Investing in Artificial Intelligence That Actually Works, Mic (2013).
6. The AIM Initiative: A Strategy for Augmenting Intelligence Using Machines, Office of the Director of National Intelligence (2019); DIA’s “MARS” Initiative Reaches Another Key Milestone, Defense Intelligence Agency Public Affairs (2021); NGA Releases New Data Strategy to Navigate Digital, GEOINT Revolution, National Geospatial-Intelligence Agency (2021); Sarah Scoles, Meet the US’s Spy System of the Future — It’s Sentient, The Verge (2019); Mark Pomerleau, NSA’s Cybersecurity Directorate Looks to Scale Up This Year, C4ISRNET (2022); Patrick Tucker, What the CIA’s Tech Director Wants from AI, Defense One (2017).
7. See e.g., Organization: Directorate of Digital Innovation, U.S. Central Intelligence Agency (last accessed 2022); Quint Forgey & Daniel Lippman, CIA Launches New China-Focused Unit, Politico (2021).
8. Steven Aftergood, Open Source Center (OSC) becomes Open Source Enterprise (OSE), Federation of American Scientists (2015); Justin Doubleday, Spy Agencies Look to Standardize Use of Open Source Intelligence, Federal News Network (2022); Justin Doubleday, State Department Intelligence Arm to Set Up Open Source Coordination Office, Federal News Network (2022).
9. Zach Dorfman & Jenna McLaughlin, The CIA’s Communications Suffered a Catastrophic Compromise. It Started in Iran, Yahoo News (2018); Zach Dorfman, Tech Giants Giving China an Edge in Espionage, Foreign Policy (2020).
10. Samantha Hoffman & Nathan Attrill, Mapping China’s Tech Giants: Supply Chains & the Global Data Collection Ecosystem, Australian Strategic Policy Institute (2021).
11. Shane Harris & Paul Sonne, Russia Planning Massive Military Offensive Against Ukraine Involving 175,000 Troops, U.S. Intelligence Warns, The Washington Post (2021).
12. Felicia Schwartz & Demetri Sevastopulo, A Real Stroke of Genius’: US Leads Efforts to Publicise Ukraine Intelligence, Financial Times (2022); Press Briefing by Press Secretary Karine Jean-Pierre and NSC Coordinator for Strategic Communications John Kirby, The White House (2022).
13. Alex Young, Too Much Information: Ineffective Intelligence Collection, Harvard International Review (2019); Cortney Weinbaum & John N.T. Shanahan, Intelligence in a Data-Driven Age, Joint Force Quarterly (2018).
14. Tomas Chamorro-Premuzic, et al., As AI Makes More Decisions, the Nature of Leadership Will Change, Harvard Business Review (2018).
15. Andrew Ng, AI Transformation Playbook, Landing AI (2020).
16. See e.g., The AIM Initiative: A Strategy for Augmenting Intelligence Using Machines, Office of the Director of National Intelligence (2019); NGA Releases New Data Strategy to Navigate Digital, GEOINT Revolution, National Geospatial-Intelligence Agency (2021).
17. Promoting Cultural Diversity in the Intelligence Community: Recruiting and Clearing Personnel with Foreign Ties, Intelligence and National Security Alliance (2022); The China Deep Dive: A Report on the Intelligence Community’s Capabilities and Competencies with Respect to the People’s Republic of China, House Permanent Select Committee on Intelligence at 28 (2020); Kenneth Lieberthal, The U.S. Intelligence Community and Foreign Policy: Getting Analysis Right, Brookings at 32-33 (2009).
18. Emily Harding, Move Over JARVIS, Meet OSCAR, Center for Strategic and International Studies at 2 (2022).
19. Digitalization of data and the spread of computers expanded the potential attack vectors again and the ability to identify who and where someone was. See Warren Strobel, Biometrics, Smartphones, Surveillance Cameras Pose New Obstacles for U.S. Spies, Wall Street Journal (2021); Hardware vulnerabilities were joined by software vulnerabilities. More and more equipment and software used by the government were commercial off-the-shelf (COTS) products – all of which could be exploited directly or through supporting services and the supply chain. See e.g., ASUS Software Updates Used for Supply Chain Attacks, Symantec Security (2019); Dina Temple-Raston, A ‘Worst Nightmare’ Cyberattack: The Untold Story Of The SolarWinds Hack, NPR (2021).
20. Corin Stone, Artificial Intelligence in the Intelligence Community: Money is Not Enough, Just Security (2021); Robert Wallace & H. Keith Melton, Spycraft: The Secret History of the CIA’s Spytechs, from Communism to Al-Qaeda, Plume at 223 (2008).
21. David Luckey, et al., Assessing Continuous Evaluation Approaches for Insider Threats: How Can the Security Posture of the U.S. Departments and Agencies Be Improved?, RAND Corporation (2019).
22. Cade Metz, A.I. Researchers Are Making More Than $1 Million, Even at a Nonprofit, New York Times (2018); The Senior Executive Service pay scale by contrast, tops out at $226,300. See Salary Table No. 2022-EX, U.S. Office of Personnel Management (2022).
23. Zachary Arnold, et al., Tracking AI Investment: Initial Findings From the Private Markets, Center for Security and Emerging Technology (2020).
24. The National Reserve Digital Corps, as envisioned by the NSCAI, would bring in digital expertise as civilian special government employees (SGEs) to work at least 38 days each year in government. The military reserves’ service commitments and incentive structure would serve as the program’s model. See Final Report, National Security Commission on Artificial Intelligence at 10, 358-362 (2021).
25. Final Report, National Security Commission on Artificial Intelligence at 127 (2021). For additional detail on technology talent pipelines for the U.S. Government, see Chapter 2 of this Report.
26. Andrew Ng, AI Transformation Playbook, Landing AI (2020).
27. The phases outlined below are drawn from a number of sources, including, SCSP Staff Engagement with AI business expert; Tomas Chamorro-Premuzic, et al., As AI Makes More Decisions, the Nature of Leadership Will Change, Harvard Business Review (2018); Andrew Ng, AI Transformation Playbook, Landing AI (2020); Manasi Vartak, How to Scale AI in Your Organization, Harvard Business Review (2022).
28. The International Data Corporation estimated that the amount of data in the world would increase from 33 Zettabytes (ZB) in 2018 to 175 ZB by 2025. One ZB is one trillion gigabytes. See David Reinsel et al., The Digitization of the World from Edge to Core, International Data Corporation at 7 (2018).
29. Report to the President of the United States, The Commission on the Intelligence Capabilities of the United States Regarding Weapons of Mass Destruction at 23, 377-380 (2005); Heather J. Williams & Ilana Blum, Defining Second Generation Open Source Intelligence (OSINT) for the Defense Enterprise, RAND Corporation (2018); Cortney Weinbaum, et al., Options for Strengthening All-Source Intelligence: Substantive Change Is Within Reach, RAND Corporation (2022).
30. SCSP staff engagement with open source experts (June 2022).
31. Herman L. Croom, The Exploitation of Foreign Open Sources, Studies in Intelligence (1969).
32. Herman L. Croom, The Exploitation of Foreign Open Sources, Studies in Intelligence (1969); Richard A. Best Jr. & Alfred Cumming, Open Source Intelligence (OSINT) Issues for Congress, Congressional Research Service at 4 (2007); Anthony Olcott, Open Source Intelligence in a Networked World, Bloomsbury at 17 (2014).
33. Preparing for the 21st Century: An Appraisal of U.S. Intelligence, Commission on the Roles and Capabilities of the United States Intelligence Community at xxi, 88-89 (1996); Roadmap for National Security: Imperative for Change, U.S. Commission on National Security/21st Century at xiv (2001).
34. Report to the President of the United States, The Commission on the Intelligence Capabilities of the United States Regarding Weapons of Mass Destruction at 23 (2005).
35. Heather J. Williams & Ilana Blum, Defining Second Generation Open Source Intelligence (OSINT) for the Defense Enterprise, RAND Corporation (2018); Cortney Weinbaum, et al., Options for Strengthening All-Source Intelligence: Substantive Change Is Within Reach, RAND Corporation (2022).
36. Federal Data Strategy, Office of Management and Budget (last accessed 2022).
37. SCSP Open Source Working Group (February 2022); Stephanie Yang, As China Shuts Out the World, Internet Access from Abroad Gets Harder Too, LA Times (2022); Sébastian Seibt, China’s Data ‘Disappearance’ Makes Information Access Rough Going for Outsiders, France 24 (2021); Glenn D. Tiffert, Peering down the Memory Hole: Censorship, Digitization, and the Fragility of Our Knowledge Base, The American Historical Review (2019).
38. Sébastian Seibt, China’s Data ‘Disappearance’ Makes Information Access Rough Going for Outsiders, France 24 (2021); Luo Jiajun & Thomas Kellogg, Verdicts from China’s Courts Used to Be Accessible Online. Now They’re Disappearing., ChinaFile (2022).
39. Josh Chin, China Is Requiring People to Register Real Names for Some Internet Services, Wall Street Journal (2015).
40. Hearing before the Subcommittee on Intelligence, Information Sharing, and Terrorism Risk Assessment of the Committee on Homeland Security, Using Open Source Information Effectively at 31 (2005).
41. For the most technology savvy version of this argument, see Emily Harding, Move Over JARVIS, Meet OSCAR, Center for Strategic and International Studies (2022).
42. Open Source Works was a small CIA unit with roughly 100 analysts who had exceptional language skills but did not have security clearances. Experienced analysts, who held security clearances, helped guide their open source collection and analysis, so that it was relevant for CIA and the U.S. Government. SCSP Staff Engagement with Retired Intelligence Official (March 2022); Gregory F. Treverton, Agenda for the Director of National Intelligence, SMA (2021).
43. At the end of 2013, OSC shut down the subscription service, citing costs, the availability of alternative sources, and potential copyright issues. See Steven Aftergood, CIA Halts Public Access to Open Source Service, Federation of American Scientists (2013); Steven Aftergood, CIA Cuts Off Public Access to Its Translated News Reports, Federation of American Scientists (2014); Steven Aftergood, Open Source Center (OSC) Becomes Open Source Enterprise (OSE), Federation of American Scientists (2015).
44. Interim National Security Strategic Guidance, The White House (2021); U.S. National Security Strategy, The White House (2017); The IC has taken steps to add leadership in this area: in 2020, the DNI established the role of Economic Security and Financial Intelligence Executive (EFX), who reports to the Deputy Director, Mission Integration. The EFX is responsible for “interagency and foreign partnership activities related to economic security, energy security, export controls, investment security, sanctions, supply chain, telecommunications, threat finance, and trade.” President Biden Announces Key National Security Nominations, The White House (2021); Additional Pre-Hearing Questions for Ms. Shannon Corless upon her nomination to be Assistant Secretary for Intelligence and Analysis, Department of the Treasury, United States Senate Select Committee on Intelligence at 4 (2021).
45. For more on a Techno-Industrial Strategy, see Chapter 2 of this report.
46. Anthony Vinci, Competitive Climate: America Must Counter China by Investing in Economic Intelligence, National Interest (2020); John Costello, et al., From Plan to Action: Operationalizing a U.S. National Technology Strategy, Center for a New American Security (2021).
47. Rush Doshi, The Long Game: China’s Grand Strategy to Displace American Order (2021).
48. The IC has taken initial steps in this direction: in 2019, ODNI established the Office of IC Net Assessment to “assess what other intelligence agencies around the world are doing and why, what the most effective technologies will be to cope with those changes, and how the world is changing strategically.” Colin Clark, IC Net Assessment: Interview With Director Flynn, Breaking Defense (2019).
49. Bennet, Sasse, Warner Unveil Legislation to Strengthen U.S. Technology Competitiveness, Senator Michael Bennet (2022).
50. S. 4503, Intelligence Authorization Act for Fiscal Year 2023 (2022).
51. Fareed Zakaria, The Future of American Power: How America Can Survive the Rise of the Rest, Foreign Affairs (2008).
52. Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China, Office of the Secretary of Defense at IV (2021).
53. Final Report, National Security Commission on AI at 161 (2021); Dennis Normile, A Beijing Think Tank Offered a Frank Review of China’s Technological Weaknesses. Then the Report Disappeared, Science (2022); Martin Placek, Share of the Global Lithium-Ion Battery Manufacturing Capacity in 2021 with a Forecast for 2025, by Country, Statista (2022); Govind Bhutada, Mapped: EV Battery Manufacturing Capacity, by Region, Visual Capitalist (2022); Lithium-ion Battery Market Size Worth $182.53 Billion By 2030: Grand View Research, Inc., Bloomberg (2022).
54. Military-Civil Fusion and the People’s Republic of China, U.S. State Department (2020).
55. Emily S. Weinstein, Beijing’s ‘re-innovation’ Strategy is Key Element of U.S.-China Competition, Brookings (2022).
56. Remarks by FBI Director Wray on The Threat Posed by the Chinese Government and the Chinese Communist Party to the Economic and National Security of the United States, Hudson Institute (2020).
57. Katerina Sedova, et al., AI and the Future of Disinformation Campaigns Part 1: The RICHDATA Framework, Center for Security and Emerging Technology (2021); Katerina Sedova, et al., AI and the Future of Disinformation Campaigns Part 2: A Threat Model, Center for Security and Emerging Technology (2021).
58. Jessica Brandt, Preempting Putin: Washington’s Campaign of Intelligence Disclosures is Complicating Moscow’s Plans for Ukraine, Brookings (2022); Douglas London, To Reveal, or Not to Reveal: The Calculus Behind U.S. Intelligence Disclosures, Foreign Affairs (2022).
59. Laura Garcia & Tommy Shane, A Guide to Prebunking: A Promising Way to Inoculate Against Misinformation, First Draft (2021).
60. Jon Roozenbeel, et al., Prebunking Interventions Based on “Inoculation” Theory Can Reduce Susceptibility to Misinformation Across Cultures, Harvard Kennedy School Misinformation Review (2020); Jonas De keersmaecker & Arne Roets, “Fake News”: Incorrect, but Hard to Correct. The Role of Cognitive Ability on the Impact of False Information on Social Impressions, Intelligence at 65, 107–110 (2017).
61. Simge Andi & Jesper Akesson, Nudging Away False News: Evidence from a Social Norms Experiment, Digital Journalism at 121 (2020).
62. National Cyber Awareness System, Cybersecurity & Infrastructure Security Agency (last accessed 2022).
63. For further discussion on individualized micro-targeting, see Chapter 5 of this report.
64. One example abroad is the targeting of U.S. Foreign Service Officer Julie Eadeh in Hong Kong. Timothy McLaughlin, How China Weaponized the Press, The Atlantic (2021). Note that micro-targeting is not limited to senior government civilian and military leaders, and also applies to kinetic attacks. For further discussion on micro-targeting, see Chapter 5 of this report.
65. Examples of recent developments include AI-enabled autonomous disinformation, texts produced by large language models, and realistic images produced by systems like DALL-E 2, OpenAI (last accessed 2022).
66. C2PA Specifications, Coalition for Content Provenance and Authenticity (2022).
67. Will Douglas Heaven, DeepMind Says Its New Language Model Can Beat Others 25 Times Its Size, MIT Technology Review (2021).
68. For further discussion of Human-Machine Teaming in the defense context, see Chapter 5 of this report.